t('Easy user management');?>
t('Admins can create, modify, search and view user accounts using Nextcloud built-in user management. Name, disk quota, mail addresses and group membership can be handled and users can be given administrator privileges if needed.');?>
t('If you need to integrate Nextcloud with an existing system, take advantage of support for one or more LDAP directories instead of or in addition to local users. Nextcloud can secure logins with two-factor authentication and supports single sign-on through SAML, OAuth2, Kerberos and others.');?>
t('For large-scale solutions, performance optimization, additional tools and advice, see the ');?>t('Nextcloud customer portal.');?>
t('Group admins');?>
t('The administrator can delegate some work by elevating some accounts to group administrator over specified groups. This allows them to create new users as members of these groups as well as delete and modify them.');?>
t('When enabled, group admins can also create 2-factor one-time login codes and do other administrative tasks like manage ACLs on Groupfolders.');?>
t('Guest accounts');?>
t('The guest accounts app enables users to create guest accounts for recipients. The administrator can determine what access rights these users need to have to external storage and apps.');?>
t('As guests have a special (hidden) group, administrators can use the Workflow and File Access Control capabilities to restrict, for example, users from downloading or sharing data. In Virtual Dataroom scenarios guest accounts can be given access to data read-only or with editing rights while blocking downloads and watermarking all files. Documents can shared with them through the Secure Mailbox feature from the Nextcloud Outlook Add-in which prevents the mail body and attachments from leaking.');?>
t('Workflow and File Access Control');?>t('Virtual data room features');?>
; ?>/assets/img/features/HaveIBeenPwned.png)
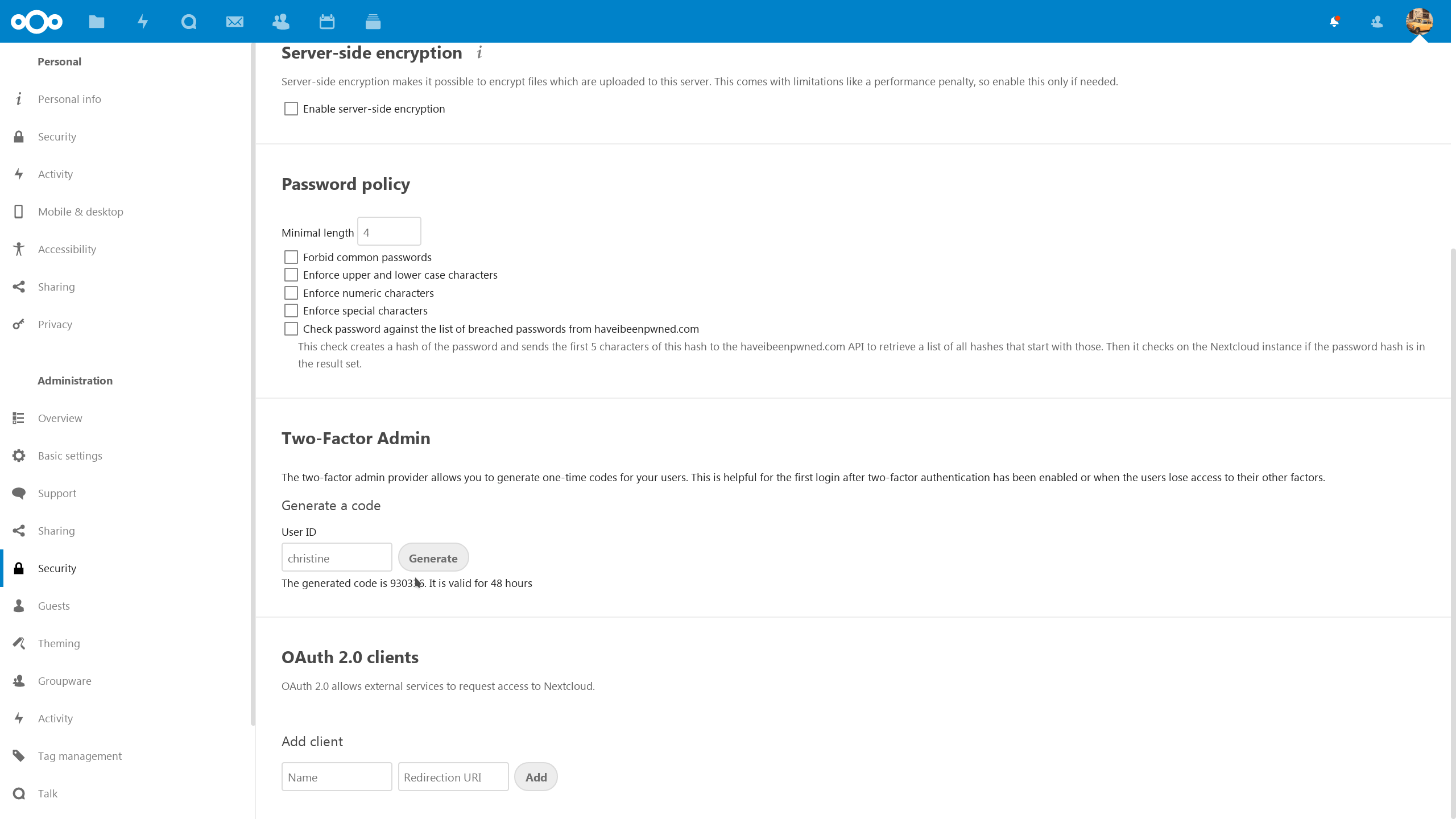
t('Password security enforcement');?>
t('Password security is extremely important and Nextcloud follows the latest and most strict standards.');?>
t('We go beyond these standards, checking passwords against the database of compromised accounts and passwords from well known security researcher Troy Hunt. This optional but highly recommended feature ensures users can not reuse a password which has been compromised on another website already. Read our blog to learn how this feature protects your users.');?>
t('Blog on HaveIBeenPwned check');?>t('Add accounts easily with a QR code');?>
t('See how easy it is for a Nextcloud user to add new accounts on their mobile devices.');?>
t('Our powerful clients are among the best rated file sync and share clients in the industry and easy to use!');?>
t('Learn about our clients');?>t('Remote Wipe');?>
t('While Nextcloud supports Mobile Device Management solutions, thanks to built-in support, remote wipe will work on systems not under management of the company. This is useful for home users but also large universities and of course in a scenario where guest accounts were handed to a third party. If you permit downloading of documents by the third party, you can wipe the documents from their devices when the the collaboration has ended.');?>
t('Remote wipe can be used on a per-device basis by users and on a per-user base by the administrator.');?>
; ?>/assets/img/features/usermanagement.png)
; ?>/assets/img/features/groupadmin.png)
; ?>/assets/img/features/guest_account.png)
; ?>/assets/img/features/remote-wipe-user.png)
; ?>/assets/img/features/remote-wipe-admin.png)
; ?>/assets/img/features/ldap.png)
; ?>/assets/img/whitepapers/ldap-thumbnail-banner.png)
; ?>/assets/img/features/api.png)
; ?>/assets/img/features/Personal_Secuity_2FA_TOTP_Setup.png)

; ?>/assets/img/features/saml.png)
; ?>/assets/img/features/gluu.png)
; ?>/assets/img/features/suspicious-login-settings.png)