diff options
| author | Huabing Zhao <zhaohuabing@gmail.com> | 2019-01-09 14:25:14 +0300 |
|---|---|---|
| committer | Huabing Zhao <zhaohuabing@gmail.com> | 2019-01-09 14:25:22 +0300 |
| commit | be8ad8dec39dc2b225cc74b377838cd8271d3329 (patch) | |
| tree | 37300cd80cdc4807c020f467481e8e60ef230ecf /exampleSite | |
| parent | 219391738716011aec2d74a00060f0e630bd4f1b (diff) | |
remove bitcoin stuff
address zhaohuabing/hugo-theme-cleanwhite#25
Signed-off-by: Huabing Zhao <zhaohuabing@gmail.com>
Diffstat (limited to 'exampleSite')
9 files changed, 157 insertions, 690 deletions
diff --git a/exampleSite/content/post/2018-05-06-cryptocurrency_week1.md b/exampleSite/content/post/2018-05-06-cryptocurrency_week1.md deleted file mode 100644 index 6468da9..0000000 --- a/exampleSite/content/post/2018-05-06-cryptocurrency_week1.md +++ /dev/null @@ -1,35 +0,0 @@ ---- -layout: post -title: "Introduction to crypto and cryptocurrencies" -subtitle: "Bitcoin and Cryptocurrency Technologies-Week 1" -date: 2018-05-06 -author: "赵化冰" -image: "https://img.zhaohuabing.com/in-post/2018-05-06-cryptocurrency_week1/bitcoin_1.jpg" -description : "I have noticed the buzzwords “Bitcoin” and “Blockchain” for a while. There are lots of articles, news, and talks around them. It seems that many people believe that cryptocurrency is the future of online payment, some even claim that blockchain would become the fundamental technology of the next generation of the Internet." -published: true -tags: - - Cryptocurrency - - Blockchain - - Bitcoin -categories: [ Note ] -URL: "/2018/05/06/cryptocurrency_week1" ---- - -> This series of articles are my notes of "Bitcoin and Cryptocurrency Technologies" online course. - -## How did I get into this? -I have noticed the buzzwords “Bitcoin” and “Blockchain” for a while. There are lots of articles, news, and talks around them. It seems that many people believe that cryptocurrency is the future of online payment, some even claim that blockchain would become the fundamental technology of the next generation of the Internet. -<!--more--> - -Given its popularity, I can’t help thinking that should I also invest in it? Maybe investing money in Bitcoin or other cryptocurrencies is too risky now, but at least I could try to learn the technologies behind these. So one day I could use this knowledge to help me estimate a potential cryptocurrency investment opportunity, or maybe find a job :-) - -## What's my finding of blockchain and cryptocurrency learning materials? -I did some searches and found so many materials about Bitcoin and Blockchain. Some of them did good jobs at explaining parts of the whole picture, But it’s a big topic so I think a systematic learning path makes more sense. - -Finally, I found this amazing “Bitcoin and Cryptocurrency Technologies” online course. It's created by the professors of Princeton University. The course has a series of well-organized lecture videos explaining the technologies behind Bitcoin from the very beginning to more advanced topics. It also has programming practices after each lecture so you can get hands in the codes and get a better understanding of the theories you got from the videos. - -I encourage anyone who is interested in cryptocurrency to attend this wonderful online course. You will not only get a chance to learn the theories and technical details behind the popular Bitcoin but also even be able to create your own version of cryptocurrency after finishing this course! The last important thing is that it's totally free! What you need to do to gain all of these is just watching the course videos and try to practice and finish your programming assignments. The course is mobile friendly, so you can even watch the course on your mobile phone when commuting on the subway, that's exactly what I'm doing, a great way to make use of the fragmented time. - -You can find the online course here: [Bitcoin and Cryptocurrency Technologies](https://www.coursera.org/learn/cryptocurrency) - -[Example codes on GitHub](https://github.com/zhaohuabing) diff --git a/exampleSite/content/post/2018-05-07-cryptocurrency_week1_cryptographic_hash_function.md b/exampleSite/content/post/2018-05-07-cryptocurrency_week1_cryptographic_hash_function.md deleted file mode 100644 index b6101ac..0000000 --- a/exampleSite/content/post/2018-05-07-cryptocurrency_week1_cryptographic_hash_function.md +++ /dev/null @@ -1,156 +0,0 @@ ---- -layout: post -title: "Cryptographic Hash Function" -subtitle: "Bitcoin and Cryptocurrency Technologies-Week 1" -date: 2018-05-09 22:00:00 -author: "赵化冰" -image: "https://img.zhaohuabing.com/in-post/2018-05-06-cryptocurrency_week1/bitcoin_3.jpg" -description: "Hash function can produce a fixed lenght digest of any size of data, and the original data can not be found out if it's properly used." -published: true -tags: - - Cryptocurrency - - Blockchain - - Bitcoin -categories: [ Note ] - -URL: "/2018/05/07/cryptocurrency_week1_cryptographic_hash_function" ---- - -> This series of articles are my notes of "Bitcoin and Cryptocurrency Technologies" online course. - -## Hash Function -Hash function is a mathematical function:*H(X)=Y* -* H: A hash function which takes an input value and calculates an output value -* X: Input of the hash function, it could be any data of any length -* Y: Output of the hash function: a fix-size bit(, it can be 256, 384, 516 ..., Bitcoin uses 256) -<!--more--> - -## Cryptographic Properties - -A hash function which is used for cryptographic purposes should have these properties: - -### Collision Free - -**Definition:** - -A hash function H is said to be collision free if: -It's infeasible to find two values X1 and X2, such that *X1!=X2*, yet *H(X1)=H(X2)* -Or in other words, -It's infeasible to find two inputs which can produce the same outputs. - -**Explaination:** - -The collision does exist because the inputs can be any data and the outputs are only 2 to 256 possibilities. - -But for a good hash function, it's just impossible to find them in an acceptable time frame even use all the computers to solve this together on the earth. - -We can use this property of hash functions to create a digest for a given data. By comparing the hash digests, we can tell if a big file is modified or corrupted during a transmission, which is often used in downloading a software. - -### Hiding - -**Definition:** - -A hash function H is hiding if: -when a secret value R is chosen from a highly spread-out distribution that, then given the hash result of *H( R/|X)*, it is infeasible to find X. /| means concatenation of two strings. - -**The Problem We Want to Solve:** - -We want a hash function that it's infeasible to find out the input by the output of a hash function. - -The problem is that if there are only a few values of inputs, it will be very easy to figure out what the input is by the output by simply trying all the possible values of inputs and see if they match the output. - -**Solution:** - -Concatenating input with a random R which is randomly chosen from a highly spread-out distribution like this: *H( R/|X)* - -**Explanation:** - -With R appended to the input, now it's infeasible to figure out what input is by just traversing all the values because there're too many possibilities. - -R is used to hide the input, by using R, the Hash function can hide the input while exposing the output. - -#### Two Uses of Hiding Property -##### 1. Commitment -This use of hiding property is explained in the lecture. - -**Scenario:** - -We want to make a commitment, keep it as a secret, and reveal it later to others. - -**Requirements:** - -* The commitment can't be seen until it's revealed -* The commitment can't be changed. -* Other people can verify the commitment once it's revealed - -**Implementation:** - -*hash(message/|key)=commitment* - -* Message: the commitment we want to make, which may only have a few values. -* Key is a generated value from a spread-out distribution used to hide the message -* commitment: the hash of message concatenated with the key - -**Explanation:** - -1. You want to make a commitment, the message, to others. It could be any message. -2. You choose a generated key which is used to hide the message. -3. You get the hash of the key message combination. -4. You publish the hash result, which is the commitment, to others and keep the key and message only to yourself. So other people know you have made a commitment, but they don't know what exactly it is. -5. After a while, you decide to reveal the commitment, so you publish the key and message. -6. Other people can use the hash function *hash(message/|key)* to calculate the hash result, compare it with the hash(commitment) you previously published. If it's the same, they can verify that you didn't change the commitment you have made. - -> * Because a key is used to hide the message, other people can't figure out what's the message before you reveal it. -> * Because of collision-free property, you can't find a message' such that *hash(message'/|key)=hash(message/|key)*, so it's impossible to change the committed message after publishing it. - -##### 2. Secure Password -Another common use of hiding property of hash is to secure passwords. - -**Scenario:** - -A website needs to verify the user password when user login. Instead of storing the password in the system, a more secure approach is just storing the hash of the password and compare the hash to verify the user. By this way, the user password won't be at risk even the system is broken by attackers because the attackers can't get the password by the hash. - -But there's still a problem, many people tend to use simple words as their passwords. Attackers can make a long list of common passwords used by people, calculate the hash of these passwords in advance, and use these hashes to attack the system to figure out what's the password. It's called a rainbow attack. - - -**Solution:** - -Use a randomly generated 'salt' to safeguard the password. - -*hash(password/|salt)=output* - -**Explanation:** - -To solve this problem, we can append a generated random value to the password, this value is often called 'salt'. Salt is saved along with the hashed password in the system. So the system can get the hash out of the combination of user password and salt, compare it with the stored hash to verify user identity. - -By appending a salt to the password, attackers can no longer use a pre-calculated password-hash map to attack the system. Even two users happened to choose the same string as their passwords, the hashes stored in the system are different because their salts are different, which is randomly generated. - -**Example:** - -> This example is excerpted from [wikipedia](https://en.wikipedia.org/wiki/Salt_(cryptography) ) - -| Username|Password|Salt value| String to be hashed|Hashed value = SHA256 (Password + Salt value)| -| ------- |--------| ---------| ---------|---------| -|user1|password123|E1F53135E559C253| password123+E1F53135E559C253| 72AE25495A7981C40622D49F9A52E4F1565C90F048F59027BD9C8C8900D5C3D8| -|user2|password123|84B03D034B409D4E|password123+84B03D034B409D4E| B4B6603ABC670967E99C7E7F1389E40CD16E78AD38EB1468EC2AA1E62B8BED3A| - -As the table above illustrates, different salt values will create completely different hashed values, even when the plaintext passwords are exactly the same. Additionally, dictionary attacks are mitigated to a degree as an attacker cannot practically precompute the hashes. However, a salt cannot protect against common or easily guessed passwords because the attacker can still combine the salt with all the possible password in the dictionary and try to match the hash of the combinations with the hashed value stored in the attached target. The salt just makes the attack more difficult because attackers need two additional steps: 1. find out the salt of the attacked target 2. Calculate the hash every time - -### Puzzle-Friendly - -**Definition:** - -A hash function H is said to be puzzle-friendly if: -Given an R which is chosen from a highly spread-out distribution and a target set Y. -Try to find a solution X such that *H(R/|X) $$/in$$ Y*. -There is no solving strategy to find X much better than just trying every possible value of X. - -**Usage:** - -Puzzle-friendly property is used for Bitcoin mining. The miner needs to find out a specific number R, which is concatenated with the data of the block, and the hash of the combination should fall into a certain range. The first one who solves this puzzle can add the outstanding transaction into the blockchain and get Bitcoin as the reward. - -Bitcoin Minding Puzzle: find R such that *H(R/|BlockData) $$/in$$ ValidRange* - -## SHA-256 -SHA-256 is the hash function used in Bitcoin which has all the three needed properties. - diff --git a/exampleSite/content/post/2018-05-12-cryptocurrency_week1_digital_signature.md b/exampleSite/content/post/2018-05-12-cryptocurrency_week1_digital_signature.md deleted file mode 100644 index aa1b1c1..0000000 --- a/exampleSite/content/post/2018-05-12-cryptocurrency_week1_digital_signature.md +++ /dev/null @@ -1,87 +0,0 @@ ---- -layout: post -title: "Digital Signature and Public Key as Identities" -subtitle: "Bitcoin and Cryptocurrency Technologies-Week 1" -date: 2018-05-15 -author: "赵化冰" -description: "Some fundamental cryptographic technologies in Bitcoin: Asymmetic encryption(Public/Private key), Digital Signature, Digital Identity(Public key and Digital Certificate)." -image: "https://img.zhaohuabing.com/in-post/2018-05-06-cryptocurrency_week1/bitcoin_header.jpg" -published: true -tags: - - Cryptocurrency - - Blockchain - - Bitcoin - - Digital Signature -categories: [ Note ] -URL: "/2018/05/12/cryptocurrency_week1_digital_signature" - ---- - -> This series of articles are my notes of "Bitcoin and Cryptocurrency Technologies" online course. -<!--more--> - -## Digital Signature -Just like a written signature of a document, but it's in digital form. The desired features: -* Only you can sign your own signature -* Everyone can verify your signature -* A signature is tied to a certain document, it can't be copied and used with other documents -<!--more--> - -## How to Sign and Verify a Digital Signature -### Generate a Pair of Public Key and Secrete/Private Key -**(sk, pk) := generates(keysize)** - -The mathematics feature of public/private key pair: Messages encrypted with private can only be decrypted with the public key, and vice versa. -You keep the private key to yourself and publish the public key to others. -Because only you have the private key, so if anyone who receives an encrypted message and the message can be decrypted with your public key, they can make sure that the message is sent from you. -### Sign a Message with the Private Key -**signature: = sign(sk, message)** - -We usually sign the hash of the message rather than the message itself. -It's because singing a fixed size hash(such as 256 bit) is much more efficient than signing a long message, and the collision-free feature of hash function can assure that no one can forge another message which has the same hash. -So the sign function is like: -**signature := encrypt(sk, hash(message))** -### Verify the Signature with Message -Others receive a message with a signature which is claimed to be sent by the signer. -They verify the message with the public key of the signer, which has already been published to all. -**isValid := verify(pk, message, signature)** - -Like I mentioned before, we usually sign the hash of the message, so the verify function is like: -**isValid := isEqual(decrypt(pk, hash(message)), signature)** - - -## Use Digital Signature with Cryptocurrency -Signing a hash pointer is identical to signing the whole structure of the data in the hash pointer points to. -* Sign the head hash pointer of a blockchain(LinkedList) is identical to sign all the transaction data in the blockchain -* Sign the root of a Merkle tree is identical to sign all the transaction data in the Merkle tree - -Explanation: -Because modification of any part in the data structure will result inconsistent at the head/root, so as long as we have verified the digital signature of the head/root, we can know for sure that the whole structure can't be forged because no one can create a fake data structure with the same head/root. - -## Public Key as Identities - -Because only the owner of the public key knowns the matching private key, so only the owner can send out a message signed with that private key. - -If we can verify the signature of a message with a public key,we can be sure that message has been sent out on behalf of the person behind of that public key,in other word,the public key is an identity of that person. - -There are two kinds of identities -### Certificated Identities - In some cases, such as signing a business contract or sending an email, you need to let the other side know who you are and able to verify your true identity, such as your name, your organization, so they can trust you when doing business with you. - -But how can people make sure the public key they received is the original one it is claimed to be? How can people know that the public key has not been modified by a middleman or it is not forged by an attacker? - -To solve this kind of trust issues in the public key publishing process, we introduced the digital certificate, which is a document consists of a public key, user identity and a signature of a trusted authority. The public key of the trusted authority has already been planted into operating systems or browsers, it's called root certificate. - -Obtain a digital certifacte from an authority - -Verify a digital signature using a certificate issued by an authority - - -### Anonymous Identities -Sometimes, you may want to keep anonymous, in that case, you just publish your public key without a certification. One example is the identiy in Bitcoin, you might not want to let others known how many money you have, especially you have a lot and prefer to keep a low profile. - -Even without certification, you can still use that anonymous identity(the public key) to do business with others as long as the people don't care who exactly you are. - -## Example Codes on GitHub -* [Digital Signature example in Java](https://github.com/zhaohuabing/digital-signature) - diff --git a/exampleSite/content/post/2018-05-12-cryptocurrency_week1_hash_pointer_and_data_structures.md b/exampleSite/content/post/2018-05-12-cryptocurrency_week1_hash_pointer_and_data_structures.md deleted file mode 100644 index f95e714..0000000 --- a/exampleSite/content/post/2018-05-12-cryptocurrency_week1_hash_pointer_and_data_structures.md +++ /dev/null @@ -1,64 +0,0 @@ ---- -layout: post -title: "Hash Pointers and Data Structures" -subtitle: "Bitcoin and Cryptocurrency Technologies-Week 1" -author: "赵化冰" -date: 2018-05-12 -image: "https://img.zhaohuabing.com/in-post/2018-05-06-cryptocurrency_week1/blockchain.png" -published: true -description: "Hash pointer is used to bulid some key data structures in cryptocurrency, such as Block chain and Merkel tree." -tags: - - Cryptocurrency - - Blockchain - - Bitcoin -categories: [ "Note" ] -URL:: "/2018/05/12/cryptocurrency_week1_hash_pointer_and_data_structures/" - ---- - -> This series of articles are my notes of "Bitcoin and Cryptocurrency Technologies" online course. - -## Hash Pointer -Hash Pointer is comprised of two parts: -* Pointer to where some information is stored -* Cryptographic hash of that information -The pointer can be used to get the information, the hash can be used to verify that information hasn't been changed - -<!--more--> - -## Data Structures Built with Hash Pointers - -### Blockchain -Hash pointers can be used to build a linked list, which is also called a blockchain. - - -We should Note that the hash stored in the hash pointer is the hash of the whole data of the previous block, which also includes the hash pointer to the block before that one. This makes it's impossible to tamper a block in the blockchain without letting others know. - -**Tamper Evident Property of Blockchain** -We only need to keep the hash pointer to the last block of the blockchain. Then when somebody shows the whole blockchain later and claim the data in it is not modified, we can tell if any block in the chain is tampered by traversing the blocks backwards and verifying the hashes one by one. - -**Explanation** -* An attacker wants to tamper with one block of the chain, let's say, block 1. -* The attacker changed the content of block 1, because of "collision free" property of the hash function, he is not able to find another data which has the same hash with the old one. So now the hash of this modified block is also changed. -* To avoid others noticing the inconsistency, he also needs to change the hash pointer of that block in the next block, which is block 2. -* Now the content of block 2 is changed, so to make this story consistent, the hash pointer in block3 must be changed. -* Finally, the attacker goes to the hash pointer to the last block of the blockchain, which is a roadblock for him, because we keep and remember that hash pointer. - - - -### Merkle Tree -Merkle tree is a binary tree building with hash pointers. The leaves are data blocks, nodes further up in the tree are the hashes of their respective children. - - - -**Features** -* **Tamper evident** -Just like blockchain, we only need to remember the hash pointer in the root (top-level node), then we can traverse down to any leaf data block to check if a node is in the tree or has it been tampered with. -* **Traversal efficiency** -To verify a data block, we only need to traverse the path from the top to the leaf where the data is. So the complexity is O(log n), which is much more efficient compared with O(n) of a linked list blockchain. -* **None-membership proof** -If Merkel tree is sorted, we can prove a given data is not in the tree: if the data before and after the given data are both in the tree and they're consecutive, so there's no space between them, this proves that the given data is not in three. - -## Example Codes on GitHub -* [Blockchain Implementation in Java](https://github.com/zhaohuabing/blockchain) -* [Merkle Tree Implementation in Java](https://github.com/zhaohuabing/merkle-tree) diff --git a/exampleSite/content/post/2018-05-20-cryptocurrency_week1_scroogecoin.md b/exampleSite/content/post/2018-05-20-cryptocurrency_week1_scroogecoin.md deleted file mode 100644 index d6b7e15..0000000 --- a/exampleSite/content/post/2018-05-20-cryptocurrency_week1_scroogecoin.md +++ /dev/null @@ -1,181 +0,0 @@ ---- -layout: post -title: "Programming Assignment: Scrooge Coin" -subtitle: "Bitcoin and Cryptocurrency Technologies-Week 1" -date: 2018-05-20 -author: "赵化冰" -description: "Finally, I got to the most exciting part of week 1 lectures-the programming assignment!" -image: "https://img.zhaohuabing.com/in-post/2018-05-06-cryptocurrency_week1/programming.jpg" -published: true -tags: - - Cryptocurrency - - Bitcoin -categories: [ Note ] -URL: "/2018/05/20/cryptocurrency_week1_scroogecoin/" - ---- - -> This series of articles are my notes of "Bitcoin and Cryptocurrency Technologies" online course. - -Finally, I got to the most exciting part of week 1 lectures-the programming assignment! -<!--more--> -I'm supposed to submit the assignment earlier because it was due a few weeks ago, however, I'd like to keep my pace relatively slow. I can't invest my full time to this course because I have a job to do, so I only take this course in my spare time. I also would like to digest all the information in one lesson before moving on to the next. Some fundamental technologies such as hash function, hash pointer, blockchain, Merkel tree and digital signature have been well-explained in week 1 lectures. In order to better understand these technologies, I also did some searches and programming practices, which can be found in my previous posts. - -<!--more--> -It turns out that writing posts on my blog is a better way to learn, I have to fully understand the lessons before I can explain them in my posts. - -## Scrooge Coin Transaction -Scrooge Coin programming assignment is a little bit tricky, the video of this lesson hasn't explained some implementation details. To help you understand the transaction data structure used in Scrooge Coin, I draw this diagram: - - -Every transaction has a set of inputs and a set of outputs. An input in a transaction must use a hash pointer to refer to its corresponding output in the previous transaction, and it must be signed with the private key of the owner because the owner needs to prove he/she agrees to spend his/her coins. - -Every output is correlated to the public key of the receiver, which is his/her ScroogeCoin address. - -In the first transaction, we assume that Scrooge has created 10 coins and assigned them to himself, we don't doubt that because the system-Scroogecoin has a building rule which says that Scrooge has right to create coins. - -In the second transaction, Scrooge transferred 3.9 coins to Alice and 5.9 coins to Bob. The sum of the two outputs is 0.2 less than the input because the transaction fee was 0.2 coin. - -In the third transaction, there were two inputs and one output, Alice and Bob transferred 9.7 coins to mike, and the transaction fee was 0.1 coin. - -## Unclaimed transaction outputs pool -Another trick we need to Note when doing the programming assignment is that an UTXOPool is introduced to track the unclaimed outputs (unspent coins), so we can know whether the corresponding output of an input of the transaction is available or not. - -## TxHandler Java Code -``` -import java.security.PublicKey; -import java.util.ArrayList; -import java.util.HashSet; -import java.util.List; -import java.util.Set; - -public class TxHandler { - private UTXOPool utxoPool; - - /** - * Creates a public ledger whose current UTXOPool (collection of unspent - * transaction outputs) is {@code utxoPool}. This should make a copy of utxoPool - * by using the UTXOPool(UTXOPool uPool) constructor. - */ - public TxHandler(UTXOPool utxoPool) { - this.utxoPool = new UTXOPool(utxoPool); - } - - /** - * @return true if: (1) all outputs claimed by {@code tx} are in the current - * UTXO pool, (2) the signatures on each input of {@code tx} are valid, - * (3) no UTXO is claimed multiple times by {@code tx}, (4) all of - * {@code tx}s output values are non-negative, and (5) the sum of - * {@code tx}s input values is greater than or equal to the sum of its - * output values; and false otherwise. - */ - public boolean isValidTx(Transaction tx) { - Set<UTXO> claimedUTXO = new HashSet<UTXO>(); - double inputSum = 0; - double outputSum = 0; - - List<Transaction.Input> inputs = tx.getInputs(); - for (int i = 0; i < inputs.size(); i++) { - Transaction.Input input = inputs.get(i); - - if (!isConsumedCoinAvailable(input)) { - return false; - } - - if (!verifySignatureOfConsumeCoin(tx, i, input)) { - return false; - } - - if (isCoinConsumedMultipleTimes(claimedUTXO, input)) { - return false; - } - - UTXO utxo = new UTXO(input.prevTxHash, input.outputIndex); - Transaction.Output correspondingOutput = utxoPool.getTxOutput(utxo); - inputSum += correspondingOutput.value; - - } - - List<Transaction.Output> outputs = tx.getOutputs(); - for (int i = 0; i < outputs.size(); i++) { - Transaction.Output output = outputs.get(i); - if (output.value <= 0) { - return false; - } - - outputSum += output.value; - } - - // Should the input value and output value be equal? Otherwise the ledger will - // become unbalanced. - // The difference between inputSum and outputSum is the transaction fee - if (outputSum > inputSum) { - return false; - } - - return true; - } - - private boolean isCoinConsumedMultipleTimes(Set<UTXO> claimedUTXO, Transaction.Input input) { - UTXO utxo = new UTXO(input.prevTxHash, input.outputIndex); - return !claimedUTXO.add(utxo); - } - - private boolean verifySignatureOfConsumeCoin(Transaction tx, int index, Transaction.Input input) { - UTXO utxo = new UTXO(input.prevTxHash, input.outputIndex); - Transaction.Output correspondingOutput = utxoPool.getTxOutput(utxo); - PublicKey pk = correspondingOutput.address; - return Crypto.verifySignature(pk, tx.getRawDataToSign(index), input.signature); - } - - private boolean isConsumedCoinAvailable(Transaction.Input input) { - UTXO utxo = new UTXO(input.prevTxHash, input.outputIndex); - return utxoPool.contains(utxo); - } - - /** - * Handles each epoch by receiving an unordered array of proposed transactions, - * checking each transaction for correctness, returning a mutually valid array - * of accepted transactions, and updating the current UTXO pool as appropriate. - */ - public Transaction[] handleTxs(Transaction[] possibleTxs) { - List<Transaction> acceptedTx = new ArrayList<Transaction>(); - for (int i = 0; i < possibleTxs.length; i++) { - Transaction tx = possibleTxs[i]; - if (isValidTx(tx)) { - acceptedTx.add(tx); - - removeConsumedCoinsFromPool(tx); - addCreatedCoinsToPool(tx); - } - } - - Transaction[] result = new Transaction[acceptedTx.size()]; - acceptedTx.toArray(result); - return result; - } - - private void addCreatedCoinsToPool(Transaction tx) { - List<Transaction.Output> outputs = tx.getOutputs(); - for (int j = 0; j < outputs.size(); j++) { - Transaction.Output output = outputs.get(j); - UTXO utxo = new UTXO(tx.getHash(), j); - utxoPool.addUTXO(utxo, output); - } - } - - private void removeConsumedCoinsFromPool(Transaction tx) { - List<Transaction.Input> inputs = tx.getInputs(); - for (int j = 0; j < inputs.size(); j++) { - Transaction.Input input = inputs.get(j); - UTXO utxo = new UTXO(input.prevTxHash, input.outputIndex); - utxoPool.removeUTXO(utxo); - } - } - -} -``` -## All the Example Codes on GitHub -I wrap the codes into a maven project, just run ```mvn test``` then the example codes will build and run all the test cases. - -[Scrooge Coin example in Java](https://github.com/zhaohuabing/scroogecoin) diff --git a/exampleSite/content/post/2018-05-27-cryptocurrency_week2_distributed_consenus.md b/exampleSite/content/post/2018-05-27-cryptocurrency_week2_distributed_consenus.md deleted file mode 100644 index 7a6a73a..0000000 --- a/exampleSite/content/post/2018-05-27-cryptocurrency_week2_distributed_consenus.md +++ /dev/null @@ -1,60 +0,0 @@ ---- -layout: post -title: "Distributed Consensus" -subtitle: "Bitcoin and Cryptocurrency Technologies-Week 2" -excerpt: "Distributed Consensus" -date: 2018-05-27 -author: "赵化冰" -image: "https://img.zhaohuabing.com/in-post/2018-05-06-cryptocurrency_week1/bitcoin_consensus.jpg" -description: "How the nodes in the bitcoin network reach consensus on the transactions?" -published: true -tags: - - Cryptocurrency - - Blockchain - - Bitcoin - - Digital Signature -categories: [ "Note" ] -URL: "/2018/05/26/cryptocurrency_week2_distributed_consenus/" ---- - -> This series of articles are my notes of "Bitcoin and Cryptocurrency Technologies" online course. -<!--more--> -## Decentralize ScroogeCoin: Distributed Consensus -Bitcoin is a peer to peer network. When Alice wants to pay Bob: -She broadcasts the transaction to all Bitcoin nodes - -The consensus of Bitcoin network: -* The content of transactions -* The order in which these transactions happened - -Transactions are put into blocks, and these blocks are linked one by one as a blockchain. -## Consensus algorithm -* New transactions are broadcast to all nodes in Bitcoin network -* Each node collects transactions into a block -* In each round a random node gets to broadcasts its block -Actually, It's the node first figure out the mathematical problem of Bitcoin -* Other nodes accept the new block only if all transactions in it are valid(unspent, valid signature) -* Nodes express their acceptance of the block by including its hash in the next block they create, in another word, put the block in their local copy of the blockchain - -## Potential attacks -### Steal other user's Bitcoin -It's impossible because attackers can't forge other user's signature, so he can't propose a valid transaction to transfer other user's coins to himself. It's the security feature of cryptographic technology Bitcoin depends on. -### Denying Services -The attacker rejects any transactions originate from a specific user. It's not a good attack because other honest nodes will propose these transactions. -### Double spending -The attacker creates two transactions, which transfer the same coins to two different addresses. In theory, these two transactions have no difference from the technology point of view. Which one is valid is only a human moral judgement. - -Solution: The rule of Bitcoin is that honest nodes always chose the longest valid branch and append the next block to that branch when there is more than one branch. So the more blocks are appended to the branch which your transaction is in, more likely this branch will be ultimately recognized by the Bitcoin network. - -The suggested number is 6, experience shows that after 6 blocks have been appended to the block which your transaction is in, you can almost be sure this branch will not become an orphan branch in the future. So if you're selling something to someone,after receiving the payment by Bitcoin, you can wait until 6 more blocks are appended next to your block, then you complete this transaction and send the payer the product. - -> There is no guarantee that a transaction is in consensus branch, but we assume the probability is almost 100% after 6 confirmation. - -I'm wondering: Does this means to avoid the potential risk of double spending attack, we always have to wait about one hour to complete a transaction? - -It seems like that, more information can be found at these two links. I think it's a big issue for Bitcoin, an hour is too long compared with nearly real-time confirmation of a traditional "centralized bank transaction". - - - -* [How long does it take for a Bitcoin transaction to be confirmed?](https://coincenter.org/entry/how-long-does-it-take-for-a-bitcoin-transaction-to-be-confirmed) -* [Average Confirmation Time of Bitcoin](https://blockchain.info/charts/avg-confirmation-time?timespan=30days) diff --git a/exampleSite/content/post/2018-05-27-cryptocurrency_week2_incentives_and_proof_of_work.md b/exampleSite/content/post/2018-05-27-cryptocurrency_week2_incentives_and_proof_of_work.md deleted file mode 100644 index cfb7479..0000000 --- a/exampleSite/content/post/2018-05-27-cryptocurrency_week2_incentives_and_proof_of_work.md +++ /dev/null @@ -1,69 +0,0 @@ ---- -layout: post - -title: "Incentives and Proof of Work" -subtitle: "Bitcoin and Cryptocurrency Technologies-Week 2" -excerpt: "Incentives and Proof of Work" -description: "How bitcoin system implements the mechanism to motivate the participants and how the participants prove their work?" -date: 2018-05-26 -author: "赵化冰" -image: "https://img.zhaohuabing.com/in-post/2018-05-06-cryptocurrency_week1/bitcoin_mining.jpg" -published: true -tags: - - Cryptocurrency - - Blockchain - - Bitcoin - - Digital Signature -categories: [ "Note" ] -URL: "/2018/05/26/cryptocurrency_week2_incentives_and_proof_of_work/" ---- - -> This series of articles are my notes of "Bitcoin and Cryptocurrency Technologies" online course. - -## Incentive -The mechanism to motivate nodes join the Bitcoin network and create blocks. -### Incentive 1: Block Reward -Creator of block gets to -* include special coin-creation transaction in the block -* choose reciptient address of this transaction (Of course, it is the miner's address) - -Explanation: Because the coin-creation transaction is just like other transaction in that block, it will only be valid if the created block ends up in the consensus chain, it's the incentive which encourages the nodes to be honest, otherwise they can't get their rewards. - -The value of the created coin is fixed in a period of 4 years, and it halves every 4 years. -The reward of the first block(the Genesis block) was 50 BTC. Because the Genesis was created on 03/Jan/2009, now 9 years past, so the reward halved twice, the current reward is 12.5 BTC. -The total number of BTC is 21 million, at the current rate, all the BTC will be mined out around 2140. - -I would have the chance be a miner if I started this lesson in 2009, what a shame! :-( - - - -[Genesis Block](https://en.bitcoin.it/wiki/Genesis_block) -[Bitcoin Block Reward Halving Countdown](https://www.bitcoinblockhalf.com/) - -### Incentive 2: Transaction Fees -* Transaction creator can choose to make the output value less than the input value -* Remainder is a transaction fee and it goes to the block creator -Right now it's purely voluntary, like a tip. But after all the Bitcoins are mined out after 2140, it might become mandatory. - -## Proof of Work -### Why Bitcoin network needs proof of work? - -To select node who gets to propose the block based on their computing power(the proportion of computing power in the whole Bitcoin network), so the adversary can't simply create a lot of civil nodes to try to get more rewards. - -### How to prove the work? - -A hash puzzle needs computing power to solve: find a nonce to get a hash output falling into a small target space. - - - -### PoW properties -* Difficult to Compute -In Aug 2014, a node needs to try about 10^20 times to find a hash in the target space. -* parameterizable cost -Nodes automatically re-calculate the target every 2 weeks to keep the average time between blocks = 10 minutes. -It means if a miner invests a fixed amount of hardware into Bitcoin mining, as time goes by, the BTC he can find during a certain period will be less because the mining ecosystem is growing, his proportion of computing power is decreasing. -**probability(Alice wins the next block) = fraction of global hash power she controls** -Why keep the time as 10 minutes: for efficiency, this allows to keep a certain number of transactions into one block - -## Key Security Assumption -Attacks are infeasible if the majority of the miners weighted by hash power follows the protocol because the competition of hash power can ensure the probability of the next block proposing by an honest node is higher than 50%. diff --git a/exampleSite/content/post/2018-06-03-cryptocurrency_week3_bitcoin_script.md b/exampleSite/content/post/2018-06-03-cryptocurrency_week3_bitcoin_script.md deleted file mode 100644 index bab54a5..0000000 --- a/exampleSite/content/post/2018-06-03-cryptocurrency_week3_bitcoin_script.md +++ /dev/null @@ -1,38 +0,0 @@ ---- -layout: post - -title: "Bitcoin Script" -subtitle: "Bitcoin and Cryptocurrency Technologies-Week 3" -description: "Bitcoin Script is using to transfer coins instead of just signature and public key address, which allows more flexibilities for Bitcoin transactions" -author: "赵化冰" -date: 2018-06-03 -image: "https://img.zhaohuabing.com/in-post/2018-05-06-cryptocurrency_week1/bitcoin_2.jpg" -published: true -tags: - - Cryptocurrency - - Blockchain - - Bitcoin - - Digital Signature -categories: [ Note ] -URL: "/2018/06/03/cryptocurrency_week3_bitcoin_script/" ---- - -> This series of articles are my notes of "Bitcoin and Cryptocurrency Technologies" online course. - -Bitcoin Script is using to transfer coins instead of just signature and public key address, which allows more flexibilities for Bitcoin transactions. - -## A Standard Transaction -Let's say Alice wants to spend some coins she received from a previous transaction, this is how the procedure looks like. -* Alice receives some coins from a previous transaction. One of the outputs of that transaction specifies the public key of Alice to indicate that the coins in that output are transferred to Alice. -> Actually, it's the cryptographic hash of the public key in order to lower the risk that attacker might figure out the private key by the public key. -* Besides the public key hash, there's also some bitcoin script code in the output, which is called scriptPubkey. -* In transaction 2, Alice wants to spend her coin, so she gives her signature to prove that she approve this transaction. She also specifies her full public key to prove her ownership of these coins. This combination is called scriptSig. -* SctiptPubkey and ScriptSig are concatenated to form a single, completed script. This script will run on Bitcoin nodes, if the output is true, then the transaction is valid and will proceed, otherwise, it's considered as invalid and will be abandoned. - -* The most simple, standard script essentially does two things when it is executed: first, the script checks if the given public key in ScriptSig matches the public key hash in ScriptPubkey, then it validates the signature with the public key. The below table shows how the script is processed. - - -## Check Multi-Signatures -Specifies N public keys, if T out of N signatures are verified as valid, the coins can be redeemed.(T<=N) -## Reference -* https://en.bitcoin.it/wiki/Script diff --git a/exampleSite/content/post/readme.md b/exampleSite/content/post/readme.md new file mode 100644 index 0000000..61a0104 --- /dev/null +++ b/exampleSite/content/post/readme.md @@ -0,0 +1,157 @@ +--- +layout: post +title: "Clean White Theme for Hugo" +subtitle: "How to set up this theme" +date: 2019-01-09 +author: "赵化冰" +image: "https://img.zhaohuabing.com/post-bg-2015.jpg" +--- + +# Clean White Theme for Hugo + +CleanWhite is a clean, elegant, but fully functional blog theme for Hugo. Here is a live [demo site](https://zhaohuabing.com) using this theme. + +It is based on [huxblog Jekyll Theme](https://github.com/Huxpro/huxpro.github.io) +and [Clean Blog Jekyll Theme](https://github.com/BlackrockDigital/startbootstrap-clean-blog-jekyll). + +These two upstream projects have done awesome jobs to create a blog theme, what I'm doing here is porting it to Hugo, of which I like the simplicity and the much faster compiling speed. Some other features which I think could be useful, such as site search with algolia and proxy for Disqus access in China, have also been built in the CleanWhite theme. Other fancy features of upstream projects are not supported by this Hugo theme, I'd like to make it as simple as possible and only focus on blog purpose, at least for now. +While I created this theme, I followed the Hugo theme best practice and tried to make every part of the template as a replaceable partial html, so it could be much easier for you to make your customization based on it. + +## Screenshots + +**Home** +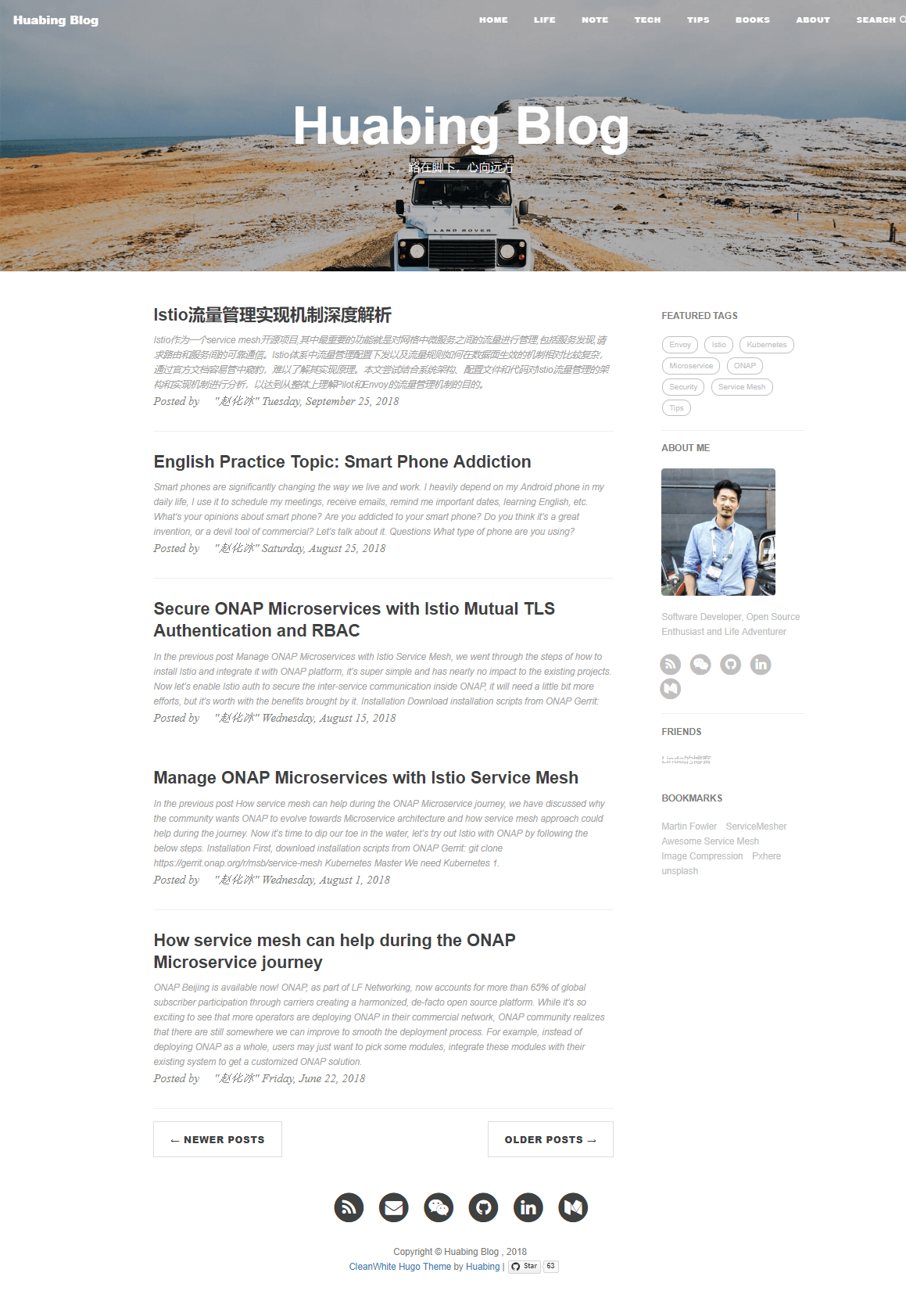 + +**Post** +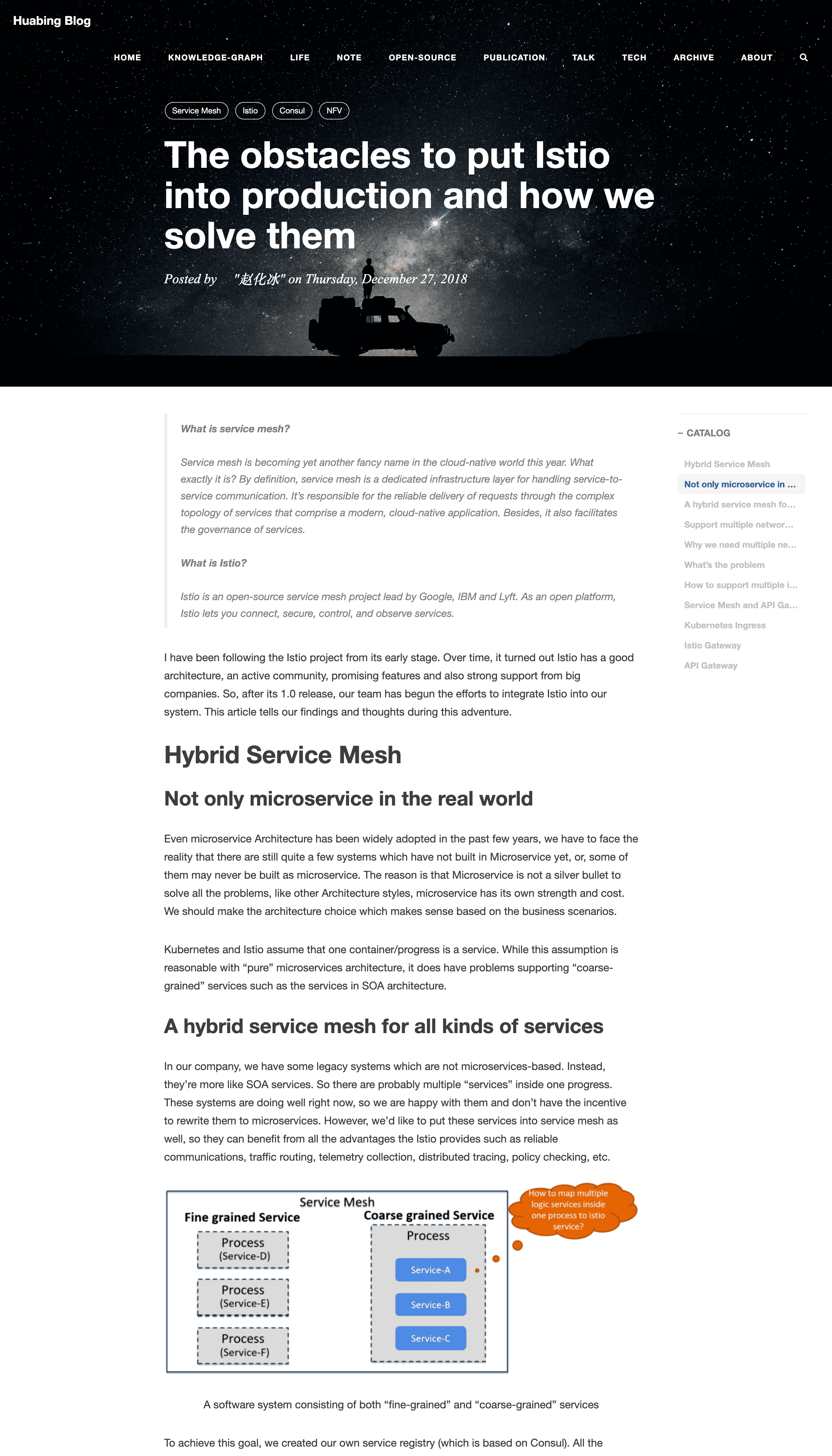 + +**Search** + + +**Wechat Pay & Alipay** + + +## Quick Start +Go to the directory where you have your Hugo site and run: + +``` +$ mkdir themes +$ cd themes +$ git clone https://github.com/zhaohuabing/hugo-theme-cleanwhite.git +``` + +If your site is already a git project, you may want to choose to add the cleanwhite theme as a submodule to avoid messing up your existing git repository. + +``` +$ mkdir themes +$ git submodule add https://github.com/zhaohuabing/hugo-theme-cleanwhite.git themes/hugo-theme-cleanwhite +``` +Run Hugo Build-in Server Locally + +``` +$ hugo serve -t hugo-theme-cleanwhite +``` +Now enter [`localhost:1313`](http://localhost:1313) in the address bar of your browser. + +If you start from scratch, there is a working Hugo site configured with the CleanWhite theme in the [exampleSite](https://github.com/zhaohuabing/hugo-theme-cleanwhite/tree/master/exampleSite) directory. You can use it as a starting point for your site. + +For more information read the official [setup guide](https://gohugo.io/overview/installing/) of Hugo + +## Configuration +First, let's take a look at the [config.toml](https://github.com/zhaohuabing/hugo-cleanwhite-theme/tree/master/exampleSite/config.toml). It will be useful to learn how to customize your site. Feel free to play around with the settings. + +### Comments +The optional comments system is powered by [Disqus](https://disqus.com). If you want to enable comments, create an account in Disqus and write down your shortname. + +```toml +disqusShortname = "your-disqus-short-name" +``` +You can disable the comments system by leaving the `disqusShortname` empty. + +### Disqus in China +Disqus is inaccessible in China. To get it to work, we can set up a proxy with [disqus-php-api](https://github.com/zhaohuabing/disqus-php-api) in a host which sets between the client browser and the Disqus server. The idea is that if Disqus can be reached in the guest network, the blog page will show the original Disqus comments UI, otherwise, it will downgrade and use the proxy to access the Disqus, the UI will be a little different, but the visitors can still write their comments on the page. + +The client side java script has already been integrated to CleanWhite them, but you need to set up a proxy server yourself. + +The proxy is written in php, which can be found here: https://github.com/zhaohuabing/disqus-php-api/tree/master/api + +You need to specify your Disqus account information in the config.php. +``` +define('PUBLIC_KEY', ''); +define('SECRET_KEY', ''); +define('DISQUS_USERNAME', ''); +define('DISQUS_EMAIL', ''); +define('DISQUS_PASSWORD', ''); +define('DISQUS_WEBSITE', ''); +define('DISQUS_SHORTNAME', ''); +``` +Set the proxy server address in the site config file of your Hugo project. +```toml +disqus_proxy = "http://yourdisqusproxy.com" +``` +### Site Search with Algolia +Follow this [tutorial](https://forestry.io/blog/search-with-algolia-in-hugo/#3-create-your-index-in-algolia) to create your index in Algolia. The index is just the storage of the indexing data of your site in the the cloud . The search page of CleanWhite theme will utilize this indexing data to do the search. + +Go to the directory where you have your Hugo site and run the following commands: +```bash +$ npm init +$ npm install atomic-algolia --save +``` +Next, open up the newly created package.json, where we’ll add an NPM script to update your index at Algolia. Find "scripts", and add the following: +```josn +"algolia": "atomic-algolia" +``` +Algolia index output format has already been supported by the CleanWhite theme, so you can just build your site, then you’ll find a file called algolia.json in the root, which we can use to update your index in Algolia. +Generate index file: +```bash +$ hugo +``` +Create a new file in the root of your Hugo project called .env, and add the following contents: +```bash +ALGOLIA_APP_ID={{ YOUR_APP_ID }} +ALGOLIA_ADMIN_KEY={{ YOUR_ADMIN_KEY }} +ALGOLIA_INDEX_NAME={{ YOUR_INDEX_NAME }} +ALGOLIA_INDEX_FILE={{ PATH/TO/algolia.json }} +``` +Now you can push your index to Algolia by simply running: +```bash +$ npm run algolia +``` +Add the following variables to your hugo site config so the search page can get access to algolia index data in the cloud: + ``` +algolia_search = true +algolia_appId = {{ YOUR_APP_ID }} +algolia_indexName = {{ YOUR_INDEX_NAME }} +algolia_apiKey = {{ YOUR_ADMIN_KEY }} +``` +Open search page in your browser: http://localhost:1313/search + +### Analytics + +You can optionally enable Google or Baidu Analytics. Type your tracking code in the + +```toml +googleAnalytics = "UA-XXXXX-X" +ba_track_id = "XXXXXXXXXXXXXXXX" +``` +Leave the `googleAnalytics` or 'ba_track_id ' key empty to disable it. + +### Wechat Pay & Alipay Rewards + +You can enable Wechat Pay & Alipay to allow readers send you money. So if they like your articles, you may even get rewards from your writing. Now you must be motivated to write more. + +* Enable Wechat Pay & Alipay in the site config +```toml +reward = true +``` +* Replace the QR codes of Wechat Pay & Alipay by overriding the photos in folder /static/img/reward/, otherwise the money will be sent to my accounts! + + +## Thank +Thanks for the great jobs of [huxblog Jekyll Theme](https://github.com/Huxpro/huxpro.github.io) and [Clean Blog Jekyll Theme](https://github.com/BlackrockDigital/startbootstrap-clean-blog-jekyll) which are the the two upstream projects CleanWhite Hugo theme is based on. + +## Feedback +If you find any problems, please feel free to [raise an issue](https://github.com/zhaohuabing/hugo-theme-cleanwhite/issues/new) or create a pull request to fix it. + +If it's helpful for you, I would appreciate it if you could star this repository, thanks! + |
